// Vulnerability Management
Protect your business from software vulnerabilities and improve your IT security
// Discover to Manage
Keep track of potential threats in your IT landscape
Cyberattacks are increasing both in number and severity, and they are getting faster. The growing complexity of IT infrastructures along with the centrality of digital solutions leave enough room for gaps, which bad actors can exploit to gain access to critical infrastructure.
In 2022, 17% of all cyberattacks were executed by ransomware. The average duration of such an attack has reduced dramatically in recent years. Today, it takes less than 3.85 days from the publication of a vulnerability to an attempted cyberattack.
Are you able to respond that quickly and eliminate vulnerabilities in your business?
// Benefits
Mitigate risks in your global IT infrastructure
Gain visibility
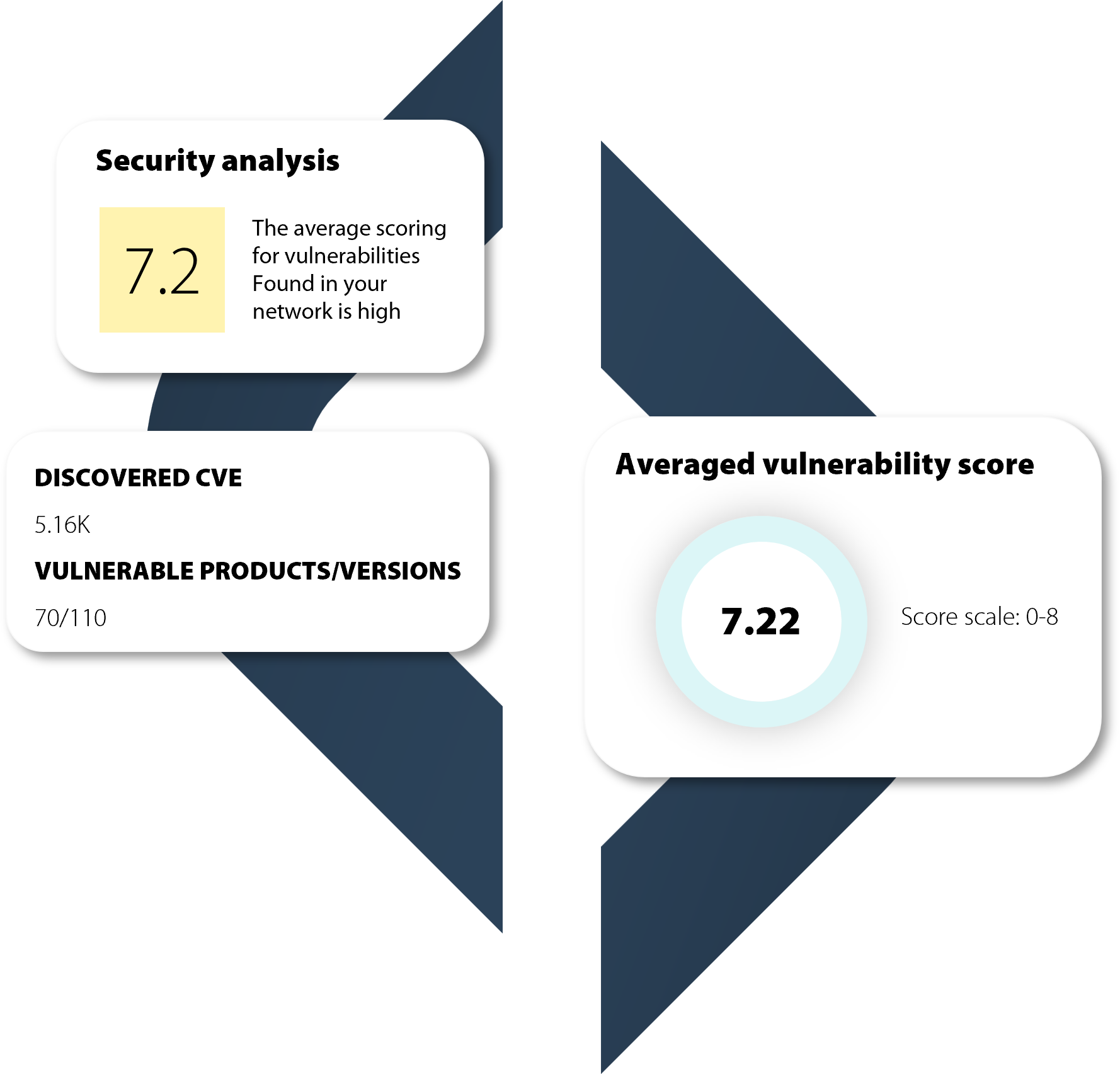
Use daily updated Information from NIST database to have an accurate overview of your vulnerabilities.
Implement automatism
Take advantage of vulnerability scoring and implement automatism for patching software vulnerabilities.
Improve IT security
Patch and update critical vulnerabilities directly after they occur and prevent unnecessary risks.
Minimize support efforts
Reduce compatibility problems and support efforts by regularly updating software vulnerabilites.
// Success story
From total IT shutdown to complete restoration in less than 2 weeks
International business group gets complete IT asset overview just days after a critical phishing attack and develops an innovative, future-proof IT security strategy.
Thanks to Raynet Technologies, the organization got the tools they needed to completely restore their digital infrastructure in just 13 days.
Customers empowered by Raynet technologies




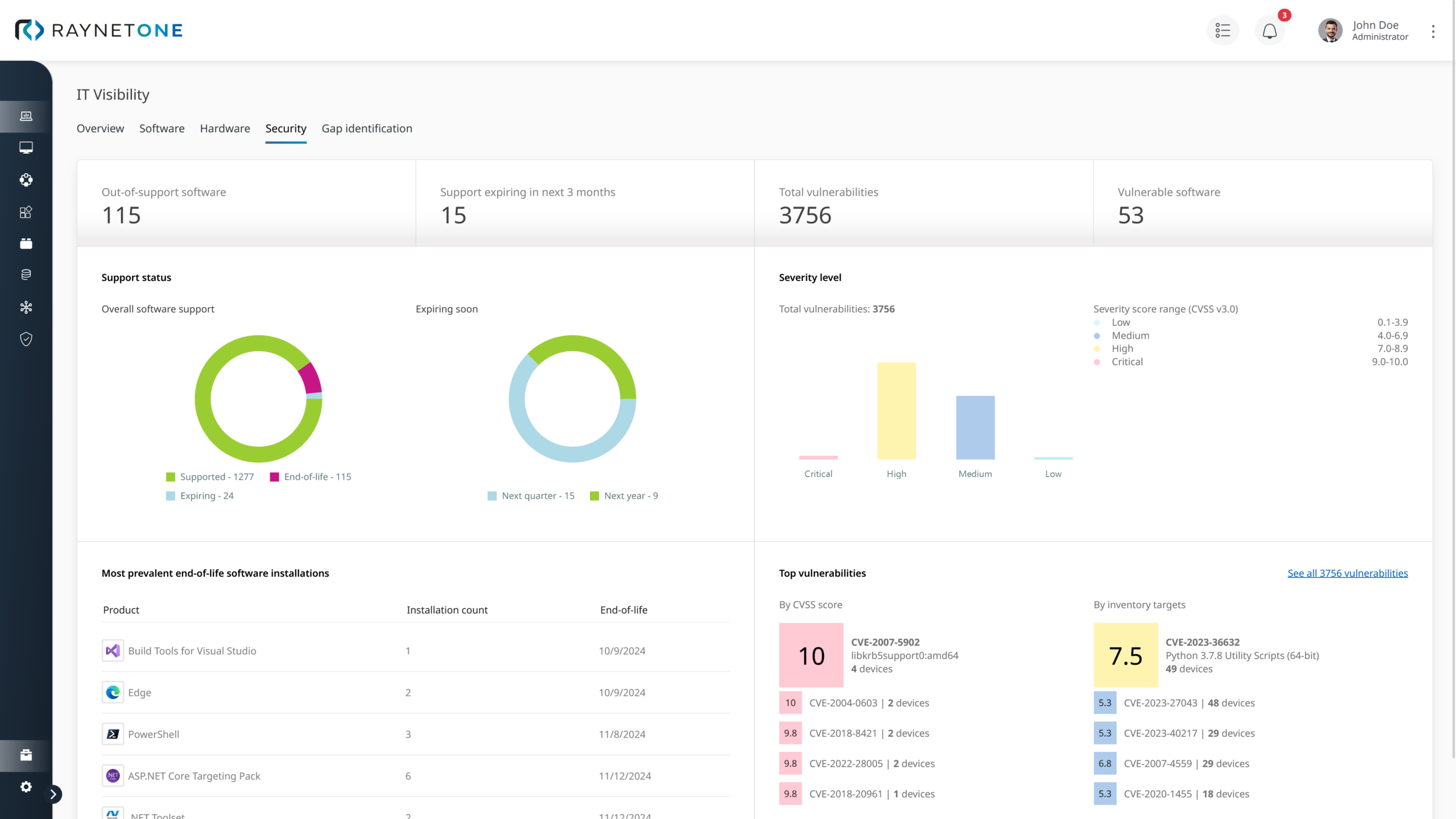
Vulnerability Management
Unsupported software no longer receives security updates, leaving your infrastructure open to user error, unmanaged vulnerabilities, and critical security gaps. Comprehensive IT Visibility is the only way to for various stakeholder to ensure they have a complete overview of their assets, including vulnerability information.
Raynet One delivers this transparency by automatically enriching your asset information with essential market data from our Technology Catalog. The Catalog is enriched daily with vulnerability information from the NIST database, giving you with accurate, reliable, and up to date vulnerability insights in meaningful dashboards.
The intelligent scoring function enables you to take immediate action to eliminate vulnerabilities, so you can protect your environment.
// Good to know
Further use cases, you might also be interested in
// We are, where you are
Contact our experts
Interested in our solutions, need further Information, or have questions?
With almost 25 years of experience and numerous customer projects worldwide, we can help you with your challenges – contact us today!
// Vulnerability Management
Protect your business from software vulnerabilities and improve your IT security
// Discover to Manage
Keep track of potential threats in your IT landscape
Cyberattacks are increasing both in number and severity, and they are getting faster. The growing complexity of IT infrastructures along with the centrality of digital solutions leave enough room for gaps, which bad actors can exploit to gain access to critical infrastructure.
In 2022, 17% of all cyberattacks were executed by ransomware. The average duration of such an attack has reduced dramatically in recent years. Today, it takes less than 3.85 days from the publication of a vulnerability to an attempted cyberattack.
Are you able to respond that quickly and eliminate vulnerabilities in your business?
// Benefits
Mitigate risks in your global IT infrastructure
Gain visibility
Use daily updated Information from NIST database to have an accurate overview of your vulnerabilities.
Implement automatism
Take advantage of vulnerability scoring and implement automatism for patching Software vulnerabilities.
Improve IT security
Patch and update critical vulnerabilities directly after they occur and prevent unnecessary risks.
Minimize support efforts
Reduce compatibility problems and support efforts by regularly updating software vulnerabilites.
// Success story
IT outage after cyber attack. Required IT transparency in less than 2 weeks
International business group gets complete IT asset overview just days after a critical phishing attack and develops an innovative, future-proof IT security strategy.
Thanks to Raynet Technologies, the organization got the tools they needed to completely restore their digital infrastructure in just 13 days.
Customers empowered by Raynet technologies




Vulnerability Management
Unsupported software no longer receives security updates, leaving your infrastructure open to user error, unmanaged vulnerabilities, and critical security gaps. Comprehensive IT Visibility is the only way to for various stakeholder to ensure they have a complete overview of their assets, including vulnerability information.
Raynet One delivers this transparency by automatically enriching your asset information with essential market data from our Technology Catalog. The Catalog is enriched daily with vulnerability information from the NIST database, giving you with accurate, reliable, and up to date vulnerability insights in meaningful dashboards.
The intelligent scoring function enables you to take immediate action to eliminate vulnerabilities, so you can protect your environment.
// Good to know
Further use cases, you might also be interested in
// We are, where you are
Contact our experts
Interested in our solutions, need further Information, or have questions?
With almost 25 years of experience and numerous customer projects worldwide, we can help you with your challenges – contact us today!