Managing directors are liable with their private assets in the event of non-compliance with the NIS 2 Directive.
NIS-2 must become law in all EU countries by mid-October this year.
According to latest research, up to 30,000 companies in Germany need to take action.
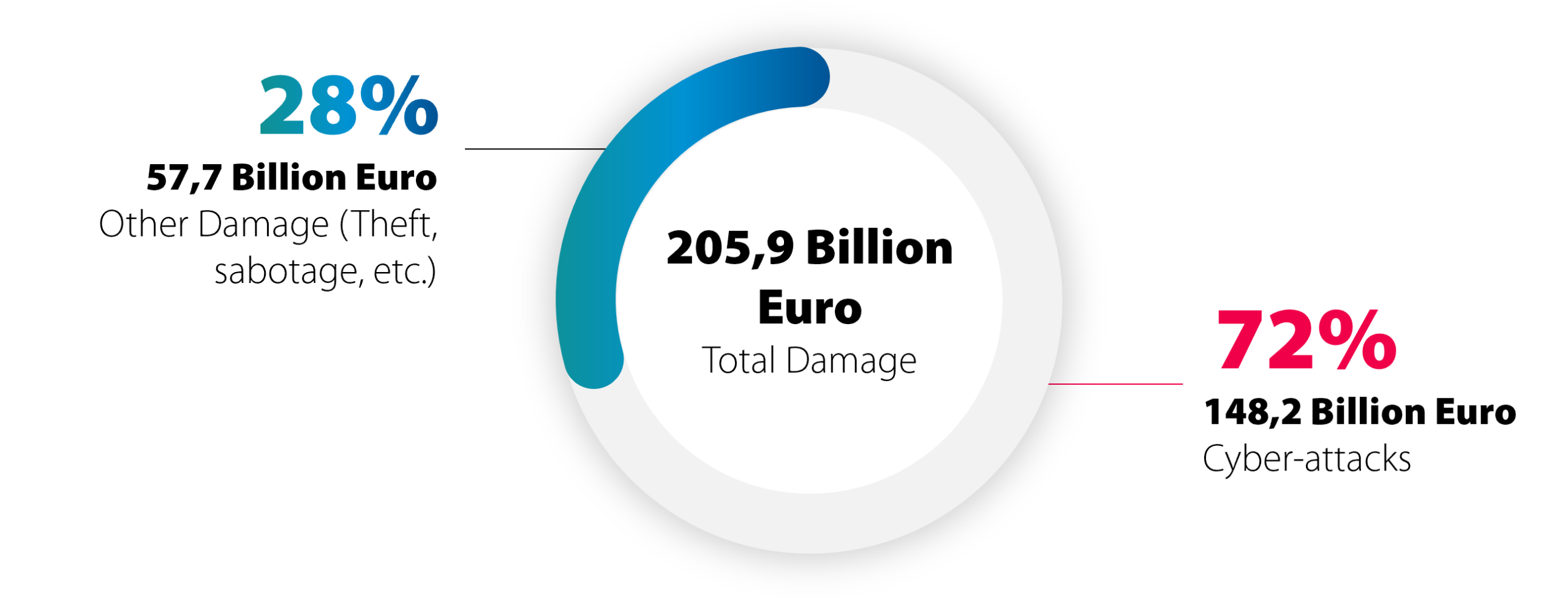
Cybersecurity experts and companies are sending alarms, as the threat of cybercrime is higher than ever before. The figures published by Bitkom e. V. confirm this: the damage caused by cybercrime in Germany amounts to a total of 205.9 billion euros. 72% of this was caused by direct cyber-attacks.
To strengthen and improve the protection of important and critical infrastructure against cyberattacks and IT threats, the European Union introduced the NIS2 Directive in 2023. This directive must be transposed into national law by all EU member states by October 17, 2024.
The states and ministries have been working on measures and draft legislation that include requirements, strategies, and standards to improve cyber security in their countries and create cyber resilience.
Many companies currently feel left alone and are in a dilemma: on the one hand, comprehensive and detailed planning is essential to meet all requirements – on the other hand, rapid implementation is necessary to avoid horrendous penalties. The key here is in the detail: the revised NIS2 Directive introduces personal liability for managing directors, board members and executive bodies – in the worst-case scenario, penalties could amount up to 2% of annual turnover.
In our blog, we have summarized the most valuable information on NIS2 for you and show why action is urgently needed now.
What is the NIS2 Directive?
NIS2 (short for Network and Information Security Directive) is the revised version of the current EU-wide NIS1 Directive. It is not new legislation but has been “tightened up” to include essential factors. NIS2 expands existing cyber security requirements in order to maximize cyber security in the EU member states.
In summary, the directive states that each EU member state must develop a national cybersecurity strategy, clearly define responsibilities and offices, draw up emergency plans, report security incidents and establish appropriate risk management.
NIS2 aims to make companies affected by the Directive more resilient and thus ensure the protection of European society in its daily life.
Who are covered by the guidelines?
The NIS2 Directive distinguishes between “essential” and “important” entities. The latter are subject to initiative-taking supervision by the authorities, while “essential entities” are subject to reactive supervision. In addition, there are “critical infrastructure operators” and federal administration facilities.
Companies from clearly defined economic sectors with a minimum turnover of 10 million euros and more than 50 employees are subject to NIS2 regulation. According to the Federal Ministry of the Interior and Community, there are almost 30,000 companies in Germany that are required to act and prepare for NIS2 compliance.
“Important entities” are large companies with at least 250 employees and a turnover of more than 50 million euros – “Essential entities” are medium-sized and large companies with at least 50 employees and a turnover of more than 10 million euros from the economic sectors:
Health
Energy
Banking
Public administration
Space
ICT service management
Digital infrastructure
Transport
Drinking water
Financial markets
Waste water
Postal and courier services
Waste management
Manufacturing
Digital providers
Research
Production, processing and distribution of food
Manufacture, production & distribution of chemicals
Source: NIS 2 Directive
The future of your IT: Why a Technology Catalog is the ultimate game changer
In this whitepaper, we’re going to show you just how a Technology Catalog can improve data quality and completeness and fuel the success of all your IT initiatives. You’ll learn:
- How a Technology Catalog makes your data more reliable
- How a Technology Catalog enriches your data to provide strategic insights
- The risks of bad data
What measures do affected companies need to implement?
Affected companies face numerous challenges: Although the NIS Directive defines specifications and requirements, it does not provide any concrete measures. Companies are forced to find solutions on their own in order to implement the requirements of NIS2 accordingly.
For companies with various European locations, it may even be the case in October that national NIS2-compliant laws already exist for some countries, but not for others.
The following obligations are relevant for all affected companies:
- Risk management measures
- Business continuity management
- Notification, registration & information obligations
- Approval, monitoring, and training obligations for managers
- Use of technical measures such as cryptography, encryption, multi-factor authentication
Additional specific requirements apply to “operators of critical systems”.
What happens in the event of non-compliance?
If the companies concerned do not comply with the required measures, they face heavy fines. “Important entities” could face fines and sanctions of up to 10 million euros or two percent of their annual turnover.
In addition, supervisory authorities have the right to monitor or issue instructions and may set deadlines to ensure that measures are implemented accordingly.
Important: The revised NIS2 Directive introduces personal liability for managing directors, board members and executive bodies. The upper limit of liability here is also two percent of annual turnover.
What are the next steps for affected companies?
Companies that are covered by the NIS2 directive must first study the relevant national law and determine steps on how to fulfill the requirements and achieve NIS2 compliance.
- Set up an internal project, define responsibilities and analyze the actual and target situation in your company
- Check which requirements from the NIS2 directive still need to be implemented. Companies that are already ISO 27001-certified cover most of the obligations
- Review your supply chains: NIS2 requires securing the entire supply chain in terms of network and information systems and the physical environment of these systems
- Define reporting processes and create emergency plans to protect your company from disaster in the event of an emergency
- Implement a cyber security solution that protects your company from threats around the clock and ensures secure business operations
IT Visibility & CAASM as the key to NIS2 compliance
The growing number and variety of solutions and digital assets make it much more difficult for a company’s IT and security teams to find the right answers to essential questions:
- Which and how many IT assets are in my IT environment?
- Which IT assets are 24/7 managed?
- Which assets have access to sensitive company data?
- Which assets are currently connected to a network?
- Which security solutions are installed on the IT assets?
- What is the security status of the IT asset?
- Which IT asset has vulnerabilities or security gaps?
The Raynet Unified Data Platform answers all this and much more with its multi-faceted approach to comprehensive IT Visibility and powerful Cyber Asset Attack Surface Management (CAASM).
While other solutions start with initial security measures and fight their way through blind spots and shadow IT, the Unified Data Platform starts with complete IT transparency. This is the only way to create meaningful and reliable insights and to plan, drive and implement the company-wide security strategy.
You can’t protect, what you can’t see!
CAASM goes beyond traditional Vulnerability Management and includes automated Third-Party & Security Patch Management, End-of-Life & End-of-Support Management and intelligent Unified Endpoint Management.
In this way, we enable fast and effective cyber security and support you in achieving a sustainable security strategy and NIS2 compliance.
Let’s talk in person and drive the success of your IT and NIS 2 initiatives together.
// Good to know
You might also be interested in
Reading time: 5 minutes
Managing directors are liable with their private assets in the event of non-compliance with the NIS 2 Directive.
NIS-2 must become law in all EU countries by mid-October this year.
According to latest research, up to 30,000 companies in Germany need to take action.
Cybersecurity experts and companies are sending alarms, as the threat of cybercrime is higher than ever before. The figures published by Bitkom e. V. confirm this: the damage caused by cybercrime in Germany amounts to a total of 205.9 billion euros. 72% of this was caused by direct cyber-attacks.
Total economic damage caused by crime in Germany
Source: Bitkom Research 2023
To strengthen and improve the protection of important and critical infrastructure against cyberattacks and IT threats, the European Union introduced the NIS2 Directive in 2023. This directive must be transposed into national law by all EU member states by October 17, 2024.
The states and ministries have been working on measures and draft legislation that include requirements, strategies, and standards to improve cyber security in their countries and create cyber resilience.
Many companies currently feel left alone and are in a dilemma: on the one hand, comprehensive and detailed planning is essential to meet all requirements – on the other hand, rapid implementation is necessary to avoid horrendous penalties. The key here is in the detail: the revised NIS2 Directive introduces personal liability for managing directors, board members and executive bodies – in the worst-case scenario, penalties could amount up to 2% of annual turnover.
In our blog, we have summarized the most valuable information on NIS2 for you and show why action is urgently needed now.
What is the NIS2 Directive?
NIS2 (short for Network and Information Security Directive) is the revised version of the current EU-wide NIS1 Directive. It is not new legislation but has been “tightened up” to include essential factors. NIS2 expands existing cyber security requirements in order to maximize cyber security in the EU member states.
In summary, the directive states that each EU member state must develop a national cybersecurity strategy, clearly define responsibilities and offices, draw up emergency plans, report security incidents and establish appropriate risk management.
NIS2 aims to make companies affected by the Directive more resilient and thus ensure the protection of European society in its daily life.
Who are covered by the guidelines?
The NIS2 Directive distinguishes between “essential” and “important” entities. The latter are subject to initiative-taking supervision by the authorities, while “essential entities” are subject to reactive supervision. In addition, there are “critical infrastructure operators” and federal administration facilities.
Companies from clearly defined economic sectors with a minimum turnover of 10 million euros and more than 50 employees are subject to NIS2 regulation. According to the Federal Ministry of the Interior and Community, there are almost 30,000 companies in Germany that are required to act and prepare for NIS2 compliance.
“Important entities” are large companies with at least 250 employees and a turnover of more than 50 million euros – “Essential entities” are medium-sized and large companies with at least 50 employees and a turnover of more than 10 million euros from the economic sectors:
Health
Energy
Banking
Public administration
Space
ICT service management
Digital infrastructure
Transport
Drinking water
Waste water
Postal & courier services
Research
Digital providers
Manufacturing
Waste management
Financial markets
Production, processing and distribution of food
Manufacture & distribution of chemicals
Source: NIS 2 Directive
The future of your IT: Why a Technology Catalog is the ultimate game changer
In this whitepaper, we’re going to show you just how a Technology Catalog can improve data quality and completeness and fuel the success of all your IT initiatives. You’ll learn:
- How a Technology Catalog makes your data more reliable
- How a Technology Catalog enriches your data to provide strategic insights
- The risks of bad data
What measures do affected companies need to implement?
Affected companies face numerous challenges: Although the NIS Directive defines specifications and requirements, it does not provide any concrete measures. Companies are forced to find solutions on their own in order to implement the requirements of NIS2 accordingly.
For companies with various European locations, it may even be the case in October that national NIS2-compliant laws already exist for some countries, but not for others.
The following obligations are relevant for all affected companies:
- Risk management measures
- Business continuity management
- Notification, registration & information obligations
- Approval, monitoring, and training obligations for managers
- Use of technical measures such as cryptography, encryption, multi-factor authentication
Additional specific requirements apply to “operators of critical systems”.
What happens in the event of non-compliance?
If the companies concerned do not comply with the required measures, they face heavy fines. “Important entities” could face fines and sanctions of up to 10 million euros or two percent of their annual turnover.
In addition, supervisory authorities have the right to monitor or issue instructions and may set deadlines to ensure that measures are implemented accordingly.
Important: The revised NIS2 Directive introduces personal liability for managing directors, board members and executive bodies. The upper limit of liability here is also two percent of annual turnover.
What are the next steps for affected companies?
Companies that are covered by the NIS2 directive must first study the relevant national law and determine steps on how to fulfill the requirements and achieve NIS2 compliance.
- Set up an internal project, define responsibilities and analyze the actual and target situation in your company
- Check which requirements from the NIS2 directive still need to be implemented. Companies that are already ISO 27001-certified cover most of the obligations
- Review your supply chains: NIS2 requires securing the entire supply chain in terms of network and information systems and the physical environment of these systems
- Define reporting processes and create emergency plans to protect your company from disaster in the event of an emergency
- Implement a cyber security solution that protects your company from threats around the clock and ensures secure business operations
IT Visibility & CAASM as the key to NIS2 compliance
The growing number and variety of solutions and digital assets make it much more difficult for a company’s IT and security teams to find the right answers to essential questions:
- Which and how many IT assets are in my IT environment?
- Which IT assets are 24/7 managed?
- Which assets have access to sensitive company data?
- Which assets are currently connected to a network?
- Which security solutions are installed on the IT assets?
- What is the security status of the IT asset?
- Which IT asset has vulnerabilities or security gaps?
The Raynet Unified Data Platform answers all this and much more with its multi-faceted approach to comprehensive IT Visibility and powerful Cyber Asset Attack Surface Management (CAASM).
While other solutions start with initial security measures and fight their way through blind spots and shadow IT, the Unified Data Platform starts with complete IT transparency. This is the only way to create meaningful and reliable insights and to plan, drive and implement the company-wide security strategy.
You can’t protect, what you can’t see!
CAASM goes beyond traditional Vulnerability Management and includes automated Third-Party & Security Patch Management, End-of-Life & End-of-Support Management and intelligent Unified Endpoint Management.
In this way, we enable fast and effective cyber security and support you in achieving a sustainable security strategy and NIS2 compliance.
Let’s talk in person and drive the success of your IT and NIS 2 initiatives together.
Share blog post: