// Intelligent Vulnerability Management
Vulnerability Management: identifying, assessing and remedying vulnerabilities
Vulnerability Management is the ongoing process of identifying, assessing, prioritising and remedying IT vulnerabilities in systems, applications and networks – before attackers can exploit them. This makes it one of the central pillars of any modern cybersecurity strategy.
The key benefits of Vulnerability Management with Raynet One
Risk-based vulnerability management: proactively overcoming cyber threats
Vulnerability Management describes the continuous process of identifying, assessing, prioritising and closing security gaps in systems, applications and networks – before attackers gain access.
Cyber attacks continue to increase worldwide – in 2025, a ransomware incident caused an average of £5.5 million in damage per company. Even more critically, less than 4 days pass on average between the publication of a vulnerability and the first attack. Companies must respond at this speed – or their infrastructure will become an easy target.
Unlike traditional vulnerability assessments, which only list gaps, risk-based Vulnerability Management (RBVM) is about prioritisation: Which vulnerabilities really threaten your business-critical systems, and where do you need to take immediate action?
Raynet One supports you throughout the entire vulnerability management lifecycle:
- automatic detection of new vulnerabilities in cloud, on-premises and remote assets,
- risk assessment with Raynet Technology Catalog, NIST and CVSS data,
- Prioritisation based on business impact and threat intelligence,
- Automated workflows for rapid patching and compliance assurance.
This allows you to minimise your attack surface, secure business operations and increase your resilience – through proactive security instead of reactive action.
Gain IT Visibility
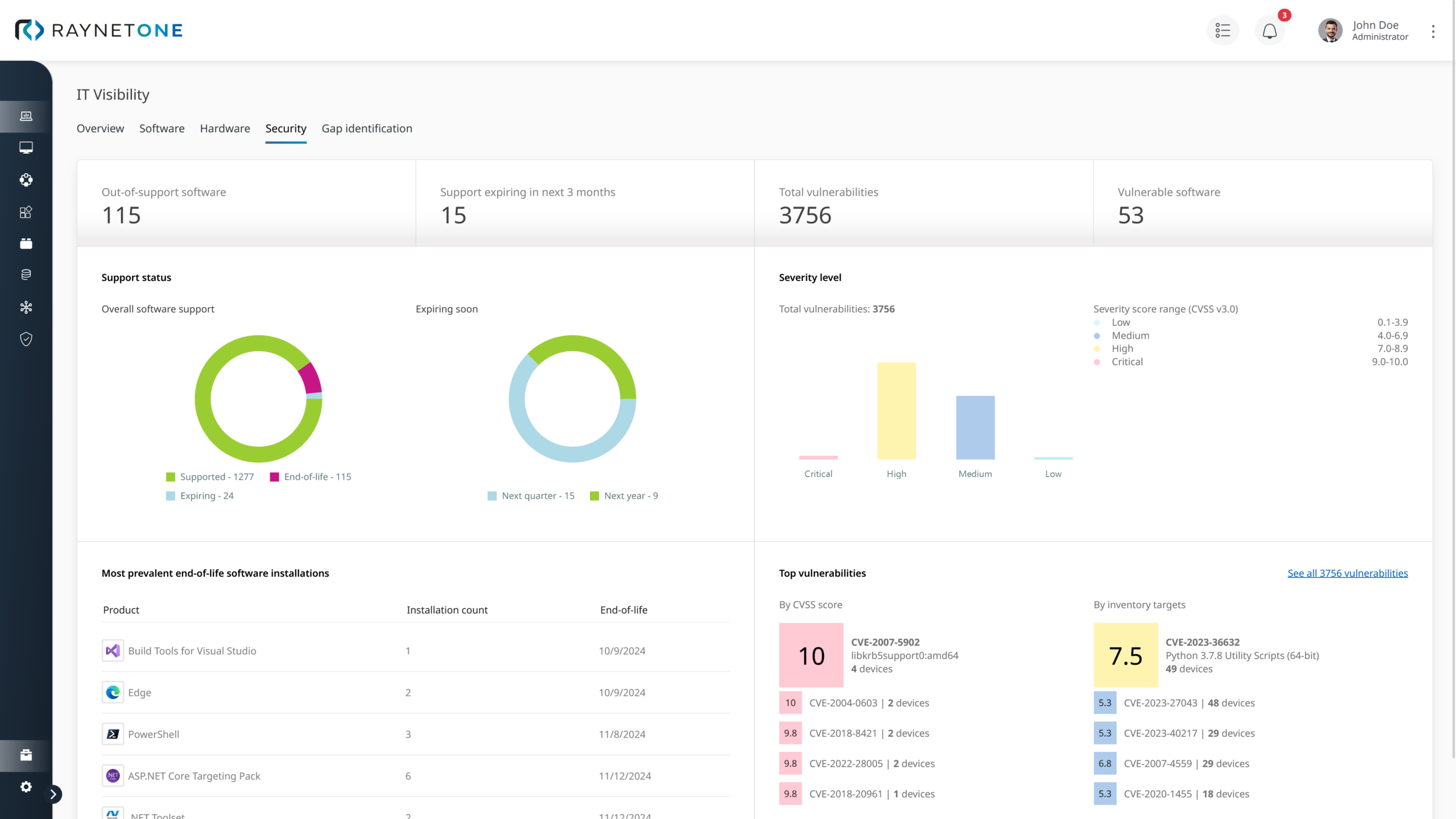
With daily updated data from NIST and the Raynet Technology Catalog, you gain full transparency over vulnerabilities in your IT – on-premises, in the cloud, and remote.
Intelligently Prioritize Risks
Our scoring models assess vulnerabilities based on criticality and exploitability. This way, you patch first what truly threatens your business.
Proactively Strengthen Security
Close critical gaps with automated patching and updates before attackers can exploit them.
Reduce Effort & Costs
Less manual work, fewer false positives: Raynet One minimizes support effort and accelerates response times (MTTR).
IT failure after cyber attack: Fully operational again in just 13 days with Raynet One Vulnerability Management
An international retail group was hit by a severe phishing attack. Within just a few hours, critical systems were paralyzed – full IT visibility was missing.
Thanks to Raynet One Vulnerability Management, the company immediately gained transparency over all affected IT assets, was able to prioritize vulnerabilities, and resolve them automatically.
The result: complete restoration of the digital infrastructure in only 13 days – combined with a sustainably improved security strategy and greater resilience.
Your company, too, can use Raynet One to detect cyberattacks faster, close vulnerabilities proactively, and minimize downtime.
Customers empowered by Raynet technologies




Vulnerability Management with Raynet One: Identify, Assess & Sustainably Resolve Risks
Effective vulnerability management is crucial for a secure IT environment. It identifies, assesses, and eliminates risks before attackers can exploit them. Unsupported software without security updates makes infrastructures particularly vulnerable – from user errors to critical security flaws.
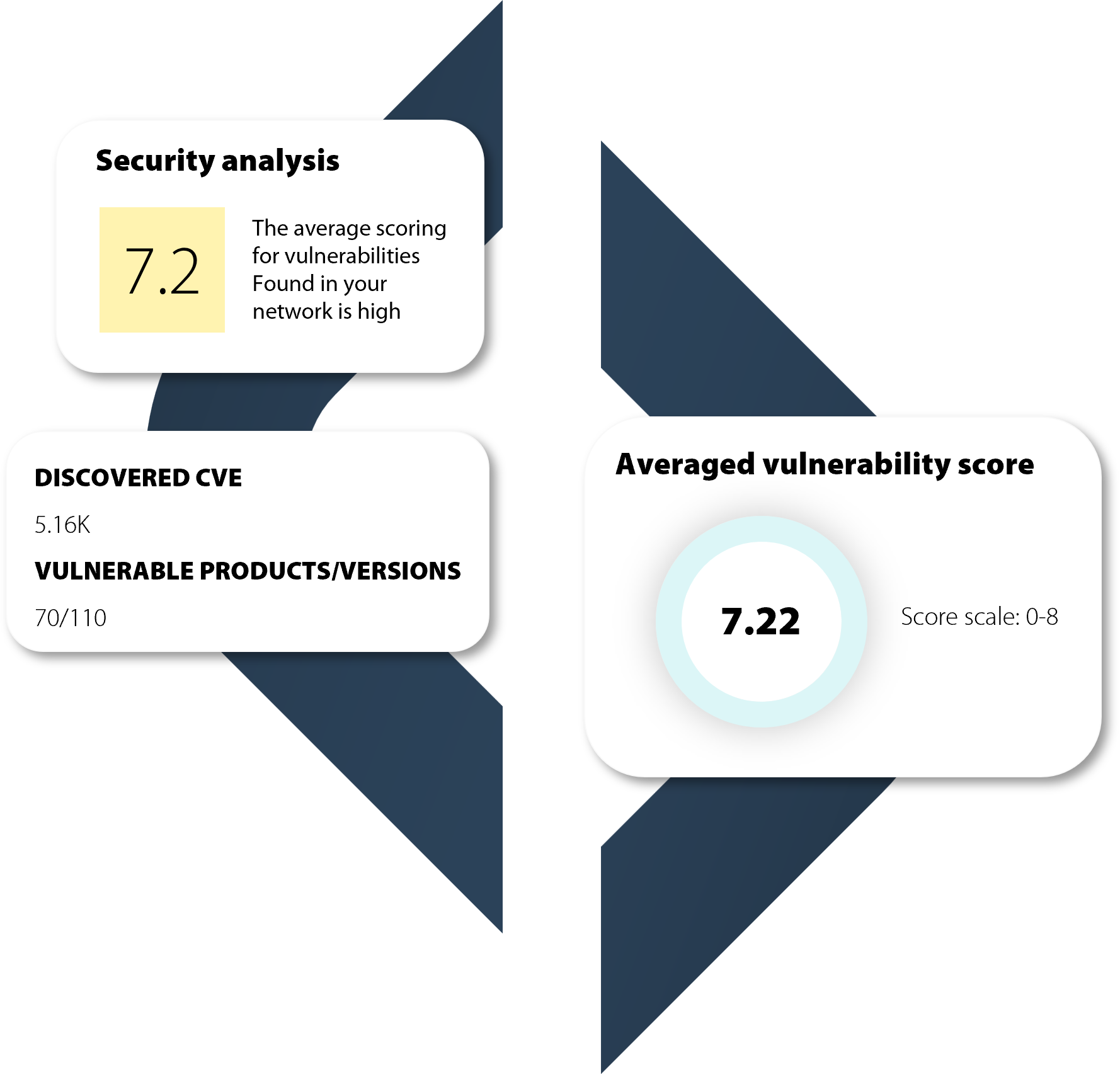
Raynet One provides the necessary transparency: the platform automatically enriches your asset data with up-to-date information from the Raynet One Technology Catalog and the NIST database. This gives you reliable, current, and context-based insights in meaningful dashboards.
But Raynet One goes beyond classic vulnerability management: with Risk-based Vulnerability Management (RBVM), not only CVSS scores are considered, but also the criticality of affected systems, exploitability, and business context. This allows you to prioritize actions exactly where they have the greatest impact on security and business continuity.
Typical vulnerabilities such as unpatched databases, outdated operating systems (e.g., Windows 7), or unupdated applications are automatically detected by Raynet One, their risks assessed, and remediation prioritized.
The integrated scoring function enables immediate actions and continuous monitoring – ensuring your IT environment remains permanently protected, audit-ready, and future-proof.
With Raynet One, you close vulnerabilities proactively – before attackers can exploit them.
Further use cases, you might also be interested in
Vulnerability Management is the ongoing process of identifying, assessing, prioritising and remedying IT vulnerabilities in systems, applications and networks – before attackers can exploit them. This makes it one of the central pillars of any modern cybersecurity strategy.
Vulnerability Management describes the continuous process of identifying, assessing, prioritising and closing security gaps in systems, applications and networks – before attackers gain access.
Cyber attacks continue to increase worldwide – in 2025, a ransomware incident caused an average of £5.5 million in damage per company. Even more critically, less than 4 days pass on average between the publication of a vulnerability and the first attack. Companies must respond at this speed – or their infrastructure will become an easy target.
Unlike traditional vulnerability assessments, which only list gaps, risk-based Vulnerability Management (RBVM) is about prioritisation: Which vulnerabilities really threaten your business-critical systems, and where do you need to take immediate action?
Raynet One supports you throughout the entire vulnerability management lifecycle:
- automatic detection of new vulnerabilities in cloud, on-premises and remote assets,
- risk assessment with Raynet Technology Catalog, NIST and CVSS data,
- Prioritisation based on business impact and threat intelligence,
- Automated workflows for rapid patching and compliance assurance.
This allows you to minimise your attack surface, secure business operations and increase your resilience – through proactive security instead of reactive action.
With daily updated data from NIST and the Raynet Technology Catalog, you gain full transparency over vulnerabilities in your IT – on-premises, in the cloud, and remote.
Our scoring models assess vulnerabilities based on criticality and exploitability. This way, you patch first what truly threatens your business.
Close critical gaps with automated patching and updates before attackers can exploit them.
Less manual work, fewer false positives: Raynet One minimizes support effort and accelerates response times (MTTR).
An international retail group was hit by a severe phishing attack. Within just a few hours, critical systems were paralyzed – full IT visibility was missing.
Thanks to Raynet One Vulnerability Management, the company immediately gained transparency over all affected IT assets, was able to prioritize vulnerabilities, and resolve them automatically.
The result: complete restoration of the digital infrastructure in only 13 days – combined with a sustainably improved security strategy and greater resilience.
Your company, too, can use Raynet One to detect cyberattacks faster, close vulnerabilities proactively, and minimize downtime.
Customers empowered by Raynet technologies




Effective vulnerability management is crucial for a secure IT environment. It identifies, assesses, and eliminates risks before attackers can exploit them. Unsupported software without security updates makes infrastructures particularly vulnerable – from user errors to critical security flaws.
Raynet One provides the necessary transparency: the platform automatically enriches your asset data with up-to-date information from the Raynet One Technology Catalog and the NIST database. This gives you reliable, current, and context-based insights in meaningful dashboards.
But Raynet One goes beyond classic vulnerability management: with Risk-based Vulnerability Management (RBVM), not only CVSS scores are considered, but also the criticality of affected systems, exploitability, and business context. This allows you to prioritize actions exactly where they have the greatest impact on security and business continuity.
Typical vulnerabilities such as unpatched databases, outdated operating systems (e.g., Windows 7), or unupdated applications are automatically detected by Raynet One, their risks assessed, and remediation prioritized.
The integrated scoring function enables immediate actions and continuous monitoring – ensuring your IT environment remains permanently protected, audit-ready, and future-proof.
With Raynet One, you close vulnerabilities proactively – before attackers can exploit them.
Frequently asked questions about Vulnerability Management
What is Vulnerability Management?
Vulnerability Management is the ongoing process of identifying, assessing and addressing IT vulnerabilities. The aim is to minimise risks before attackers can exploit security gaps.
Why is effective Vulnerability Management so important?
Cyber attacks are constantly on the rise and often occur within days of a security vulnerability being disclosed. With proactive vulnerability management, organisations can close security gaps in a timely manner and strengthen their IT resilience.
What are the advantages of Vulnerability Management with Raynet One?
Raynet One provides daily updated vulnerability information from the NIST database and automatically enriches IT data with relevant security information. This provides companies with meaningful dashboards, intelligent scoring and concrete recommendations for action.
How does Vulnerability Management support IT security in everyday life?
Automated workflows allow vulnerabilities to be quickly prioritised and patched. This reduces security risks, minimises downtime and improves IT security in the long term.
For whom is Vulnerability Management particularly relevant?
Vulnerability Management is relevant for all companies with complex IT landscapes. Security teams, IT administrators and compliance officers who need transparency about vulnerabilities and must ensure audit security benefit particularly from it.
How quickly can Vulnerability Management be implemented with Raynet One?
With Raynet One, companies get a complete overview of all relevant vulnerabilities in no time. The solution is quick to implement, scalable and integrates seamlessly into existing security and IT systems.
Contact our experts
Interested in our solutions, need further Information, or have questions?
With more than 25 years of experience and numerous customer projects worldwide, we can help you with your challenges – contact us today!