// Making attack surfaces visible
Cyber Asset Attack Surface Management: Identifying and minimizing IT risks
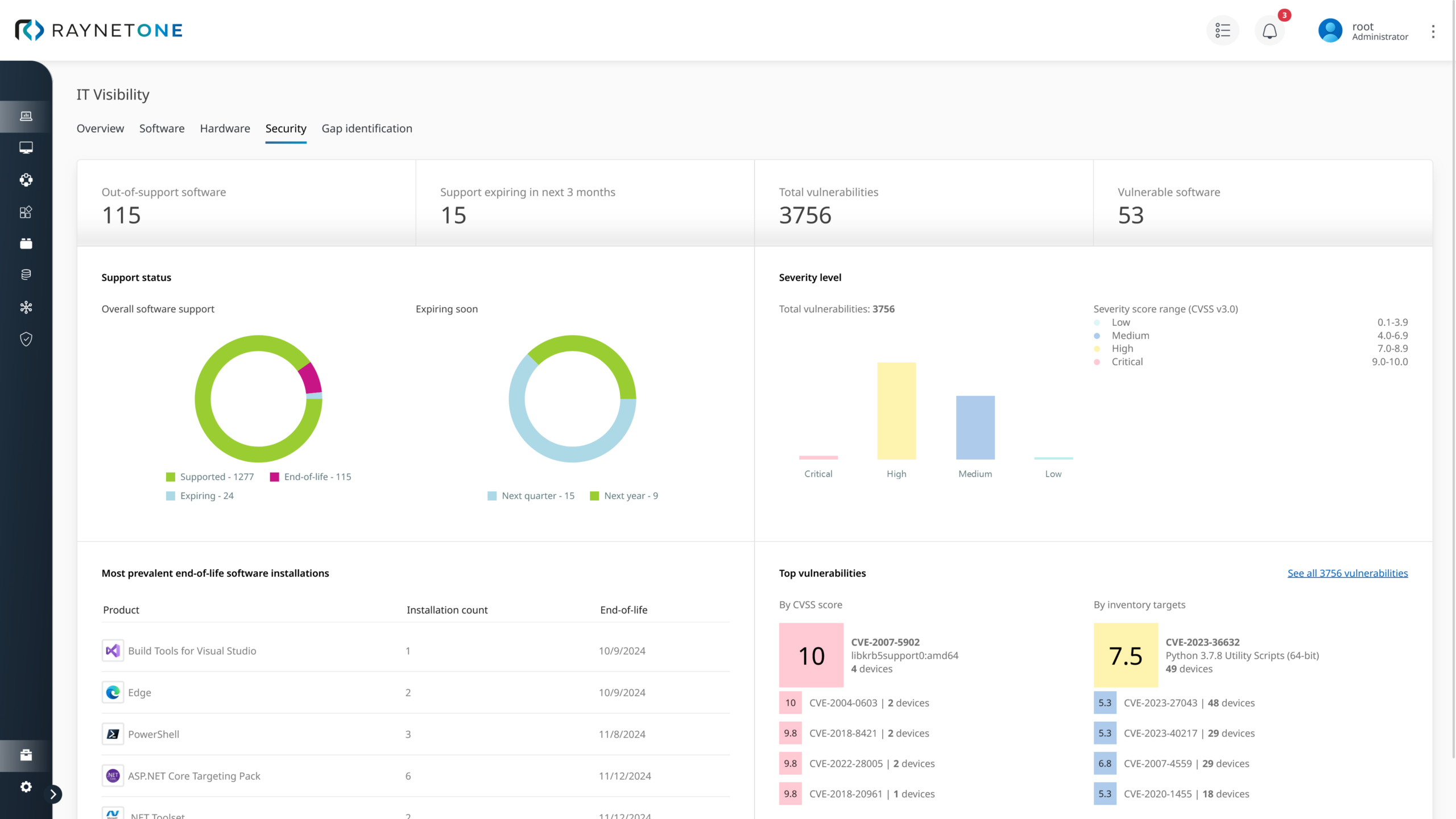
Cyber Asset Attack Surface Management (CAASM) refers to the systematic recording, consolidation and analysis of all of a company’s digital assets – from end devices and applications to identities and cloud workloads. The aim is to make the entire attack surface visible, identify risks at an early stage and proactively manage security measures.
The key benefits of Raynet One CAASM
Raynet CAASM – complete transparency and control over your attack surface
Raynet CAASM (Cyber Asset Attack Surface Management) gives companies complete visibility into all IT assets and digital attack surfaces. In times of increasing cyber threats, CAASM supports security teams in identifying risks early, reducing attack surfaces, and ensuring compliance.
With every new technology, the number of cyber assets grows – often unnoticed. Traditional solutions reach their limits: shadow IT, missing visibility, and isolated data sources create security gaps. Raynet CAASM consolidates information from existing systems and makes your entire attack surface visible in real time.
CAASM solutions like Raynet One integrate data from ITAM, CMDB, vulnerability management, and cloud platforms into a unified data foundation. This creates a central inventory of all assets, including context (user, location, business relevance) for analysis, incident response, and compliance.
How you stay in control:
Identify, analyze, and protect all cyber assets – automated, scalable, and audit-proof.
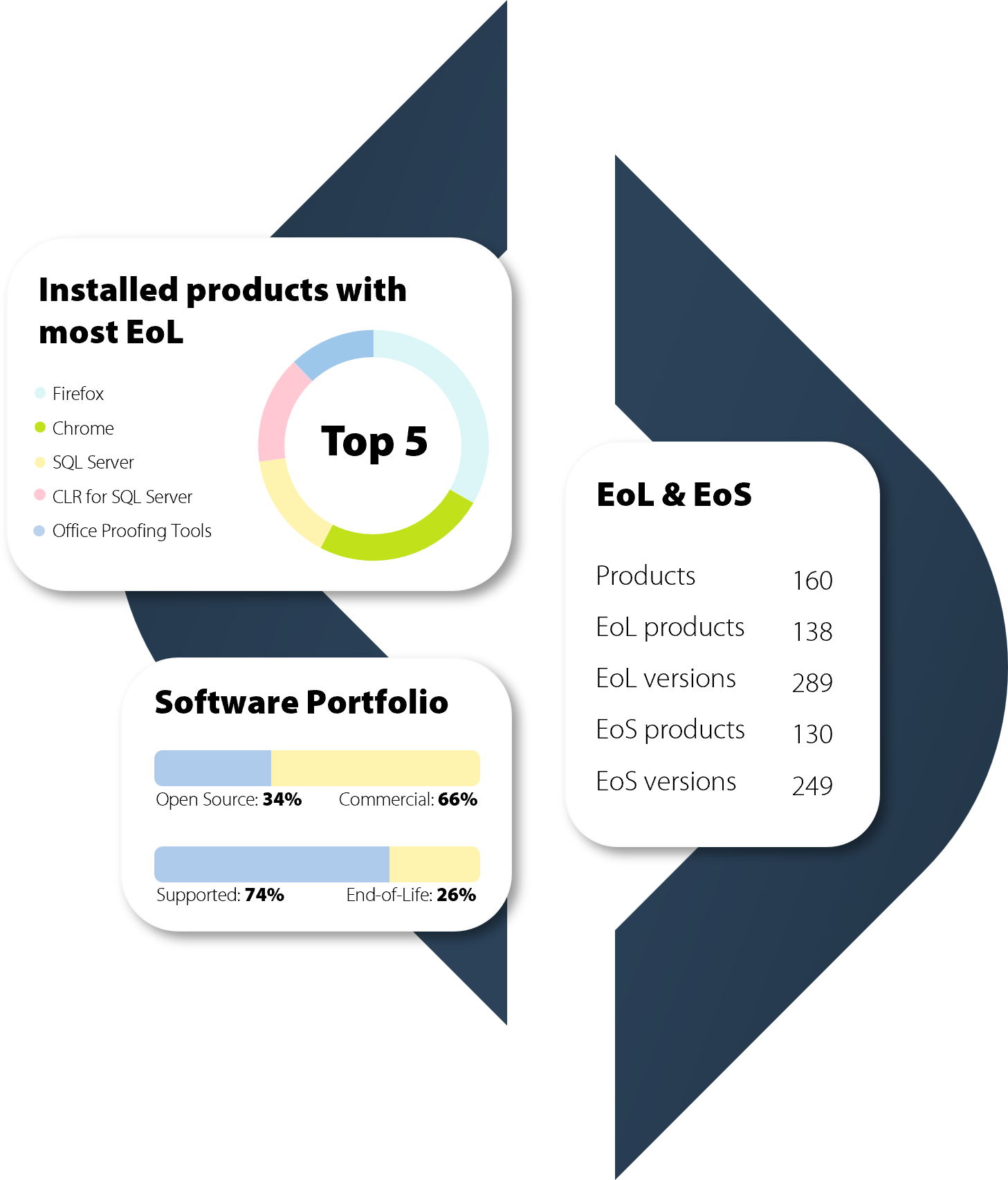
Strengthen your cyber resilience with complete asset transparency
Full Real-Time Visibility
With Raynet CAASM, you gain a central overview of all cyber assets – whether on-premises, hybrid, or cloud-based. This allows you to detect risks faster and sustainably reduce your attack surface.
Proactively Manage Risks
Continuously monitor your cyber assets, identify vulnerabilities early, and remediate them before attackers can exploit them.
Respond to Incidents Faster
Optimize your incident response: consolidated real-time data shortens Mean Time to Response (MTTR) and minimizes downtime.
Permanently Increase Security Levels
Strengthen compliance and stay one step ahead of threats – with scalable, always up-to-date security measures.
Cyber attack stopped. Complete IT transparency with Raynet in just 13 days.
An international retail group became the target of a severe phishing attack. Within hours, large parts of the IT infrastructure went down – the situation was critical.
With Raynet CAASM, the company gained immediate transparency over all affected cyber assets and was able to close security gaps in a targeted way.
After just 13 days, the entire IT environment was fully restored – more secure, more transparent, and future-ready.
Customers empowered by Raynet technologies




Full cyber asset transparency with Raynet One CAASM
You can only protect what you can see. This is exactly where Raynet One CAASM (Cyber Asset Attack Surface Management) comes in: the platform identifies all relevant cyber assets – from servers, endpoints, and IoT devices to applications, services, and databases, as well as digital identities such as user accounts and roles.
The result is a complete, centralized overview of your entire IT environment – in real time, consolidated, and immediately actionable.
Raynet One shows which systems are unprotected, where security tools are working reliably – and where they are not – as well as which vulnerabilities threaten the stability, compliance, and availability of your business processes.
This creates the foundation for data-driven decisions, continuous resilience, and a proactive IT security strategy.
Further use cases, you might also be interested in
Frequently asked questions about Cyber Asset Attack Surface Management
What is Cyber Asset Attack Surface Management?
Cyber Asset Attack Surface Management (CAASM) refers to the consolidated recording, analysis and control of all digital assets. The aim is to identify attack surfaces, detect risks at an early stage and implement security measures proactively.
What are the benefits of CAASM for businesses?
CAASM provides full transparency across all cyber assets, speeds up response times to incidents and reduces security risks. It also strengthens compliance and helps businesses to increase their cyber resilience in the long term.
Who can benefit from Cyber Asset Attack Surface Management?
CAASM is suitable for companies of all sizes that operate complex IT environments. Security teams, IT managers and compliance officers who want to minimise blind spots and shadow IT will benefit in particular.
How does CAASM differ from traditional Vulnerability Management?
While Vulnerability Management only scans for vulnerabilities, CAASM provides a comprehensive overview of all assets. This allows security measures to be prioritised, dependencies to be analysed and risks to be reduced in a targeted manner.
What role does Raynet One play in CAASM?
Raynet One integrates data from ITAM, CMDB, cloud and security tools into a unified platform. This creates True IT Asset Visibility – the basis for efficient risk analysis, compliance and a strong cybersecurity strategy.
How quickly can CAASM be implemented with Raynet One?
With Raynet One, companies can obtain an initial usable overview of their IT landscape within minutes. The solution is ready for immediate use, scalable and can be seamlessly integrated into existing systems.
Cyber Asset Attack Surface Management (CAASM) refers to the systematic recording, consolidation and analysis of all of a company’s digital assets – from end devices and applications to identities and cloud workloads. The aim is to make the entire attack surface visible, identify risks at an early stage and proactively manage security measures.
Raynet CAASM (Cyber Asset Attack Surface Management) gives companies complete visibility into all IT assets and digital attack surfaces. In times of increasing cyber threats, CAASM supports security teams in identifying risks early, reducing attack surfaces, and ensuring compliance.
With every new technology, the number of cyber assets grows – often unnoticed. Traditional solutions reach their limits: shadow IT, missing visibility, and isolated data sources create security gaps. Raynet CAASM consolidates information from existing systems and makes your entire attack surface visible in real time.
CAASM solutions like Raynet One integrate data from ITAM, CMDB, vulnerability management, and cloud platforms into a unified data foundation. This creates a central inventory of all assets, including context (user, location, business relevance) for analysis, incident response, and compliance.
How you stay in control:
Identify, analyze, and protect all cyber assets – automated, scalable, and audit-proof.
With Raynet CAASM, you gain a central overview of all cyber assets – whether on-premises, hybrid, or cloud-based. This allows you to detect risks faster and sustainably reduce your attack surface.
Continuously monitor your cyber assets, identify vulnerabilities early, and remediate them before attackers can exploit them.
Optimize your incident response: consolidated real-time data shortens Mean Time to Response (MTTR) and minimizes downtime.
Strengthen compliance and stay one step ahead of threats – with scalable, always up-to-date security measures.
An international retail group became the target of a severe phishing attack. Within hours, large parts of the IT infrastructure went down – the situation was critical.
With Raynet CAASM, the company gained immediate transparency over all affected cyber assets and was able to close security gaps in a targeted way.
After just 13 days, the entire IT environment was fully restored – more secure, more transparent, and future-ready.




You can only protect what you can see. This is exactly where Raynet One CAASM (Cyber Asset Attack Surface Management) comes in: the platform identifies all relevant cyber assets – from servers, endpoints, and IoT devices to applications, services, and databases, as well as digital identities such as user accounts and roles.
The result is a complete, centralized overview of your entire IT environment – in real time, consolidated, and immediately actionable.
Raynet One shows which systems are unprotected, where security tools are working reliably – and where they are not – as well as which vulnerabilities threaten the stability, compliance, and availability of your business processes.
This creates the foundation for data-driven decisions, continuous resilience, and a proactive IT security strategy.
What is Cyber Asset Attack Surface Management?
Cyber Asset Attack Surface Management (CAASM) refers to the consolidated recording, analysis and control of all digital assets. The aim is to identify attack surfaces, detect risks at an early stage and implement security measures proactively.
What are the benefits of CAASM for businesses?
CAASM provides full transparency across all cyber assets, speeds up response times to incidents and reduces security risks. It also strengthens compliance and helps businesses to increase their cyber resilience in the long term.
Who can benefit from Cyber Asset Attack Surface Management?
CAASM is suitable for companies of all sizes that operate complex IT environments. Security teams, IT managers and compliance officers who want to minimise blind spots and shadow IT will benefit in particular.
How does CAASM differ from traditional Vulnerability Management?
While Vulnerability Management only scans for vulnerabilities, CAASM provides a comprehensive overview of all assets. This allows security measures to be prioritised, dependencies to be analysed and risks to be reduced in a targeted manner.
What role does Raynet One play in CAASM?
Raynet One integrates data from ITAM, CMDB, cloud and security tools into a unified platform. This creates True IT Asset Visibility – the basis for efficient risk analysis, compliance and a strong cybersecurity strategy.
How quickly can CAASM be implemented with Raynet One?
With Raynet One, companies can obtain an initial usable overview of their IT landscape within minutes. The solution is ready for immediate use, scalable and can be seamlessly integrated into existing systems.
Contact our experts
Interested in our solutions, need further Information, or have questions?
With more than 25 years of experience and numerous customer projects worldwide, we can help you with your challenges – contact us today!