Securely integrate private devices into your IT infrastructure
Increasing flexibility
Reduction of hardware costs
Compliance with safety standards
Bring Your Own Device
As part of the digital transformation private smartphones, tablets and laptops have become constant companions in everyday work. To allow the use of private devices (BYOD) does not only cater to the personal preferences and satisfaction of employees but also reduces the cost of procurement of client hardware.
However, managing these devices and operating systems, some of which are decentralized, requires a considerable amount of extra work for IT in addition to its daily tasks.

BRING YOUR OWN DEVICE
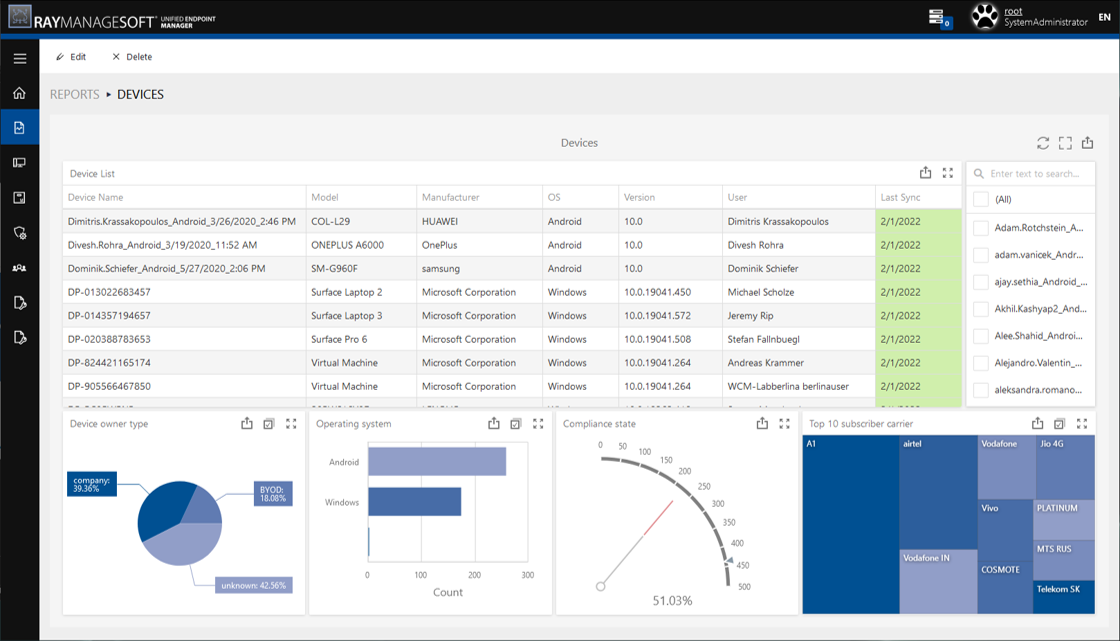
One central platform for all devices
RayManageSoft UEM enables your enterprise to manage all these additional devices on a single platform. This allows you to configure these devices and ensure the protected access on sensible business data without taking any risky detours with the data transfer. Professional and private end user environments are separated in alliance with all security standards.
Senkung der Bereitstellungskosten
für Migrationen
This might also interest you
// Success Storys
Securely integrate private devices into your IT infrastructure
Increasing
flexibility
Reduction of
hardware costs
Compliance with
safety standards
Bring Your Own Device
As part of the digital transformation private smartphones, tablets and laptops have become constant companions in everyday work. To allow the use of private devices (BYOD) does not only cater to the personal preferences and satisfaction of employees but also reduces the cost of procurement of client hardware.
However, managing these devices and operating systems, some of which are decentralized, requires a considerable amount of extra work for IT in addition to its daily tasks.

BRING YOUR OWN DEVICE
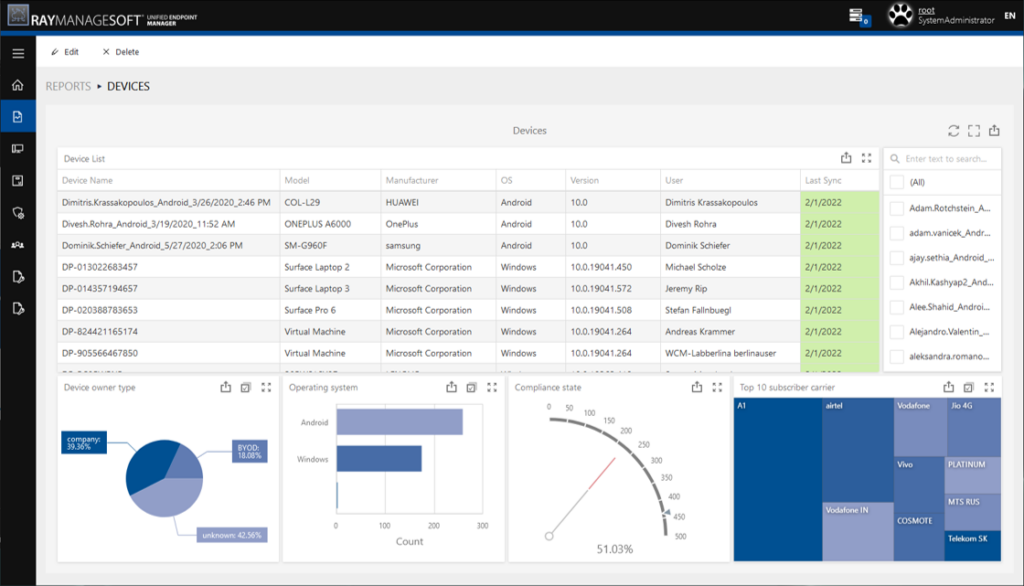
One central platform for all devices
RayManageSoft UEM enables your enterprise to manage all these additional devices on a single platform. This allows you to configure these devices and ensure the protected access on sensible business data without taking any risky detours with the data transfer. Professional and private end user environments are separated in alliance with all security standards.
You might also be interested in
// Success Storys
We're excited to help you!
Interested in our solutions, need further information, or have other questions? Reach out to us now.
